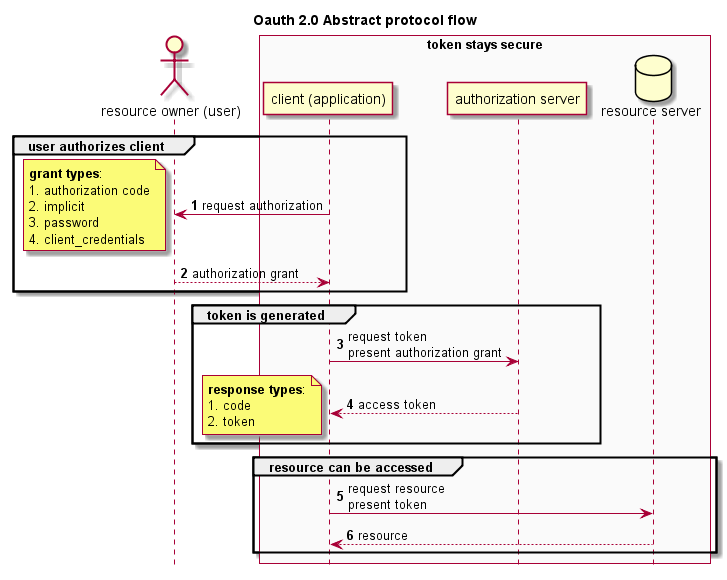
An Authentication-Oriented Approach to Model the Crosscutting Constraints in Sequence Diagram Using Aspect OCL

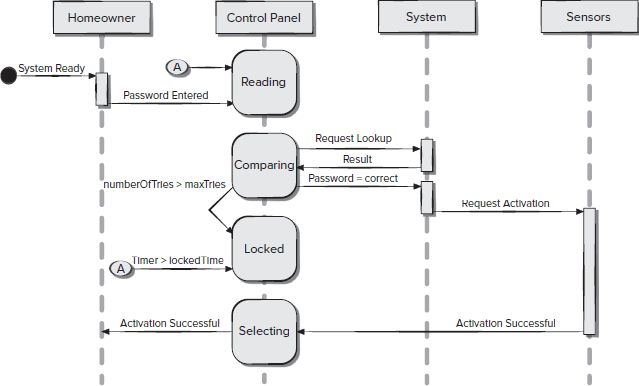
Sequence diagram of security management system (no security violation). | Download Scientific Diagram
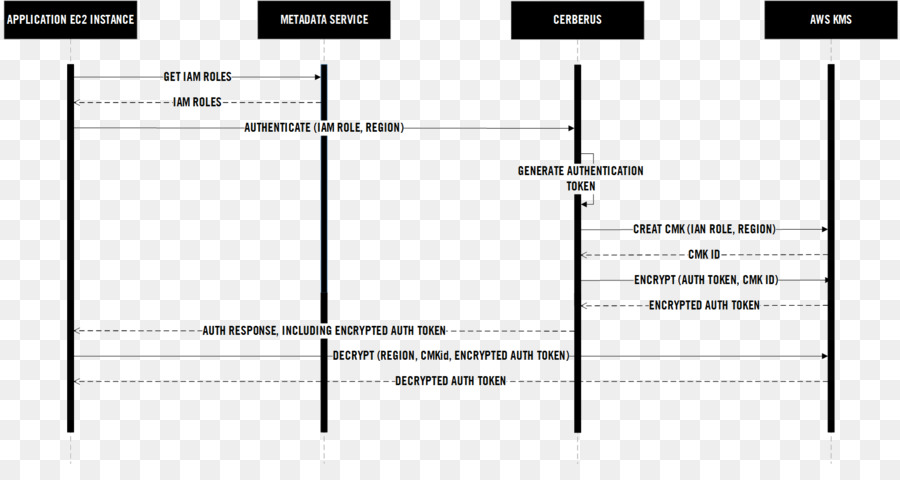
![MS-RPCE]: Packet Sequence for Secure, Connection-Oriented RPC Using NTLM as Security Provider | Microsoft Learn MS-RPCE]: Packet Sequence for Secure, Connection-Oriented RPC Using NTLM as Security Provider | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-rpce/ms-rpce_files/image023.png)
MS-RPCE]: Packet Sequence for Secure, Connection-Oriented RPC Using NTLM as Security Provider | Microsoft Learn