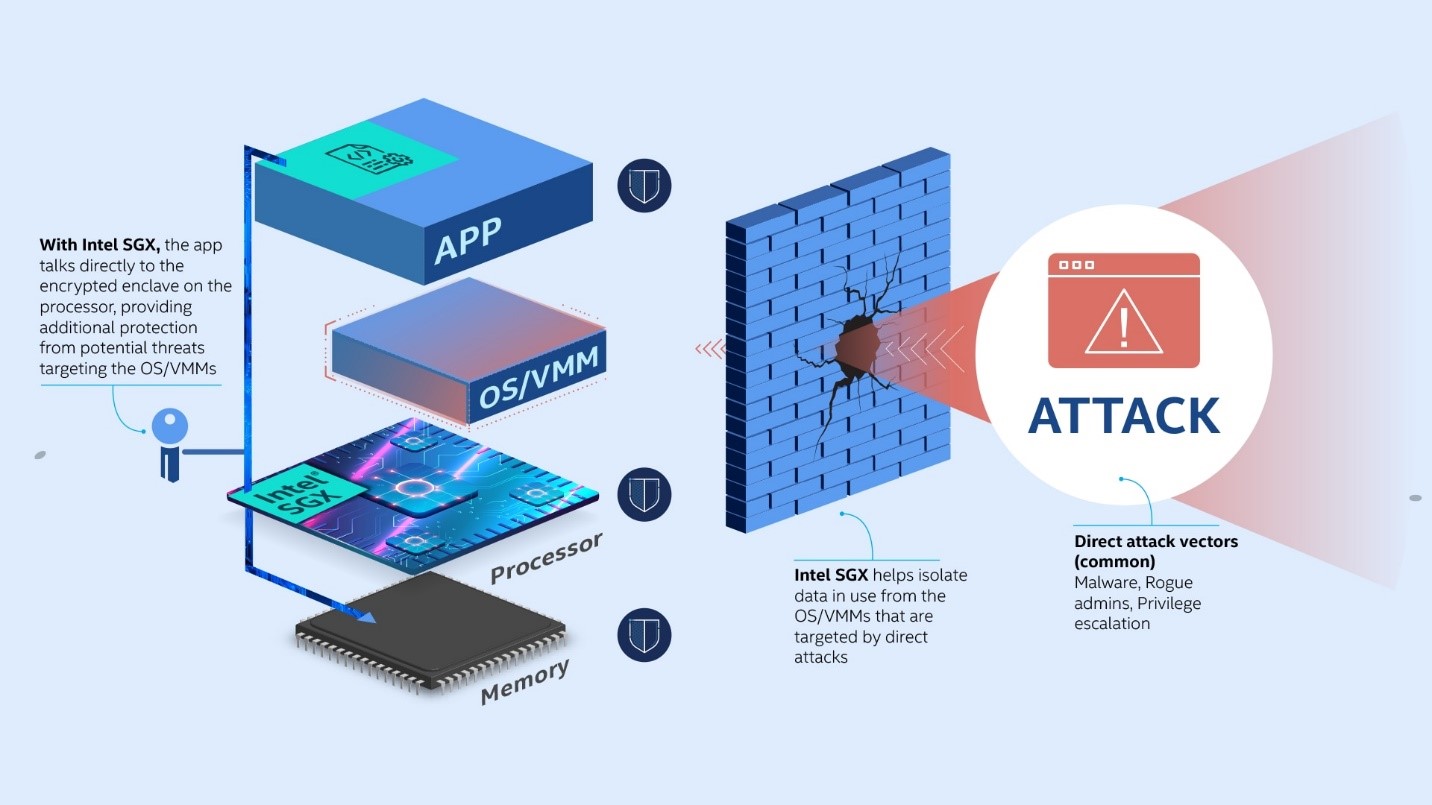
Real time detection of cache-based side-channel attacks using hardware performance counters - ScienceDirect
Hardware-based attacks based on different entities in the semiconductor... | Download Scientific Diagram

A survey on physical unclonable function (PUF)-based security solutions for Internet of Things - ScienceDirect



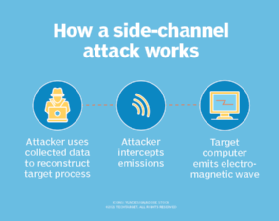









![PDF] Hardware Security, Vulnerabilities, and Attacks: A Comprehensive Taxonomy | Semantic Scholar PDF] Hardware Security, Vulnerabilities, and Attacks: A Comprehensive Taxonomy | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1fac9e722cd47fa28222a53bb4d624a42d0d0d04/3-Figure2-1.png)