Amazon.com: Security Key C NFC by Yubico - Black - FIDO U2F and FIDO 2 only - Two Factor authentication Hardware Security Key : Electronics

File:U2F Hardware Authentication Security Keys (Yubico Yubikey 4 and Feitian MultiPass FIDO) (42286852310).jpg - Wikimedia Commons

OnlyKey FIDO2 / U2F Security Key and Hardware Password Manager | Universal Two Factor Authentication | Portable Professional Grade Encryption | PGP/SSH/Yubikey OTP | Windows/Linux/Mac OS/Android : Amazon.in: Electronics

Examples of three hardware tokens, i.e., devices generating one-time... | Download Scientific Diagram

Amazon.com: Yubico Security Key, YubiKey 5, NFC Login, U2F, FIDO2, USB-A Ports, Dual Verification, Heavy Duty, Shock Resistant, Waterproof : Electronics

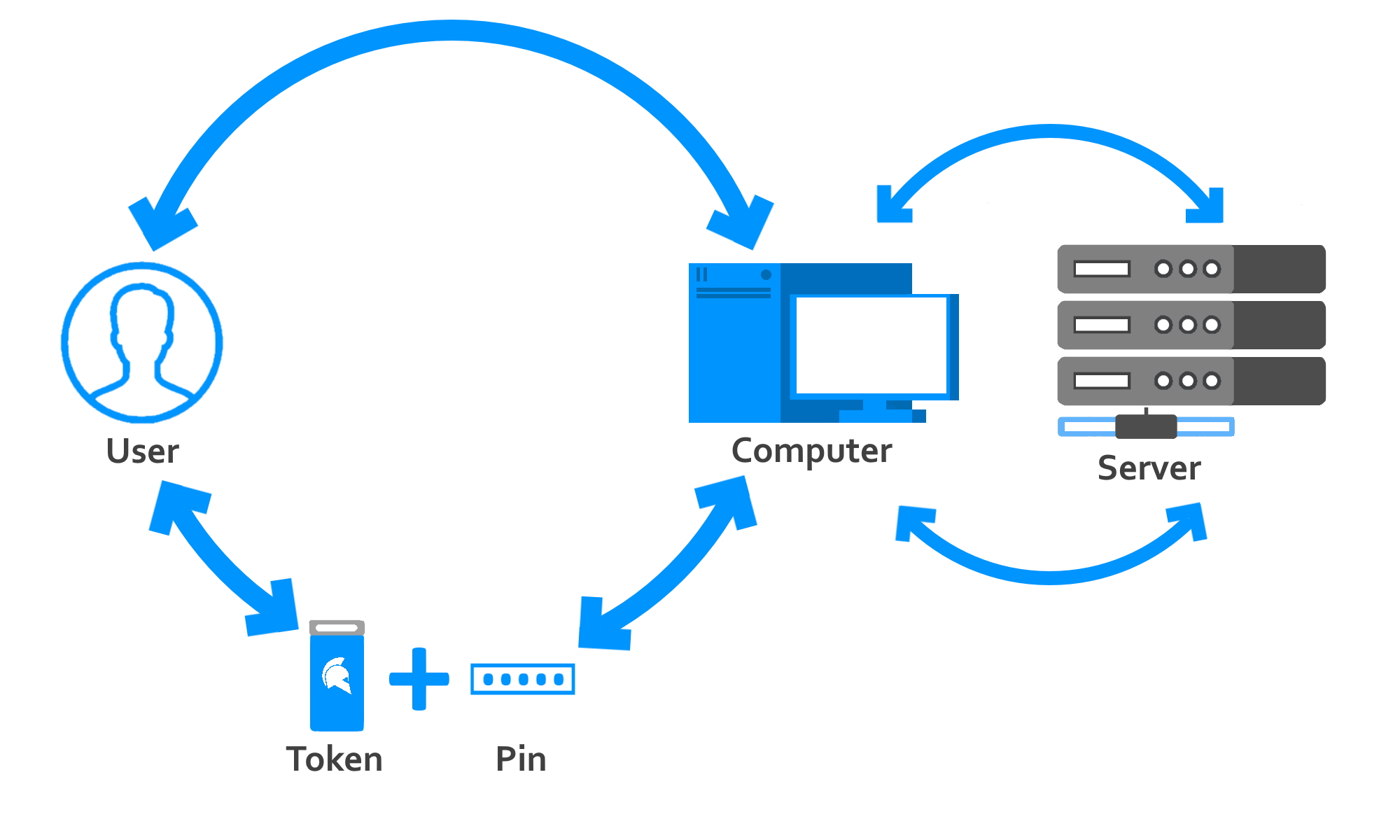
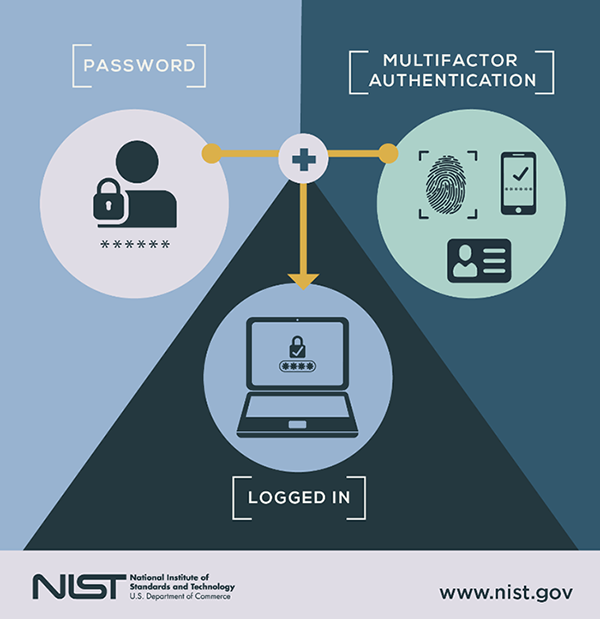
Can I use a hardware token for 2FA (Two-Factor Authentication) - Submit an Idea - monday Community Forum

YubiKey Hardware Authentication Device for Telecommuting Editorial Photo - Image of yubico, office: 200397881