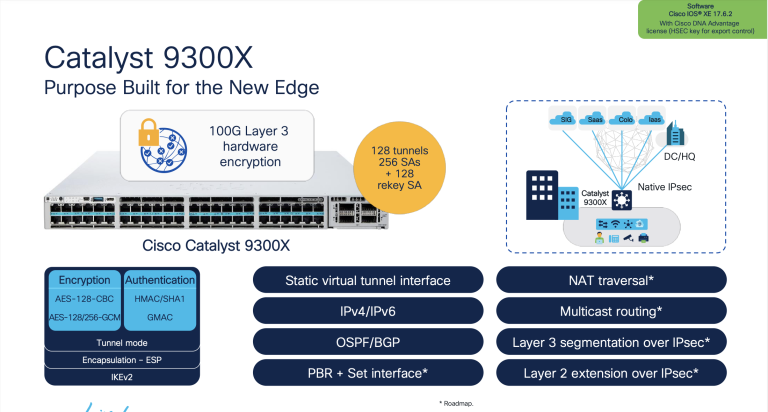
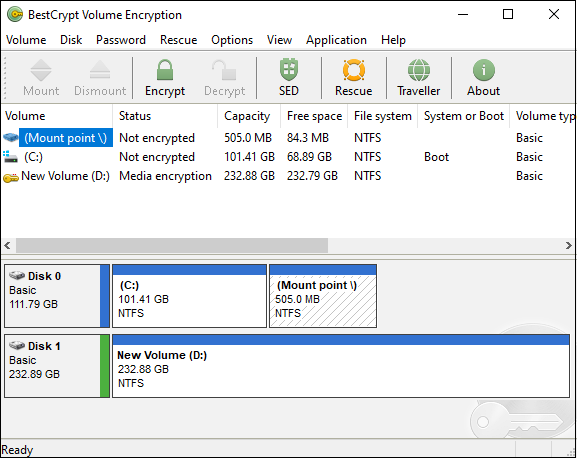
Hardware Accelerated BitLocker Encryption: Microsoft Windows 8 eDrive Investigated with Crucial M500

Encryption Done Right & Drive Configurations - The Crucial/Micron M500 Review (960GB, 480GB, 240GB, 120GB)

iStorage CloudAshur Hardware Security Module - Password Protected, Dust and Water Resistant, Portable, Military Grade Hardware Encryption - 5 Factor Authentication IS-EM-CA-256: Amazon.de: Computer & Zubehör

Kanguru: The One-Stop Solution for AES 256-Bit Hardware Encryption and Fully-Integrated Remote Management | Business Wire