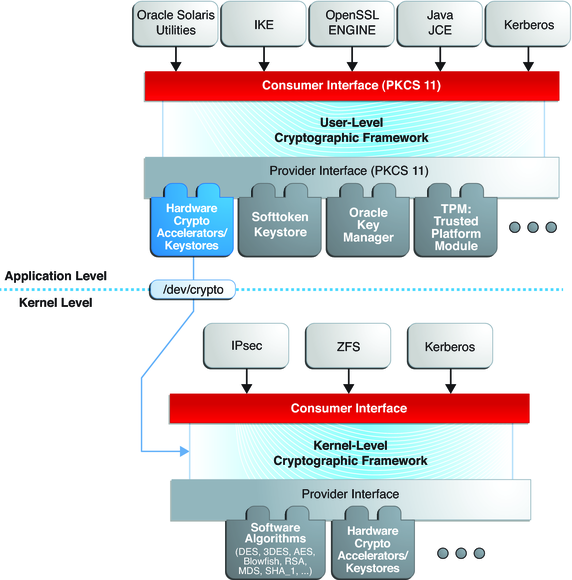
Kryptor FGPA is a Hardware Security Module that adds Complex Open-source Encryption - Electronics-Lab.com
Automated cryptocode generator is helping secure the web | MIT News | Massachusetts Institute of Technology

Why Hardware Encryption is More Effective Than Software Encryption For Securing The Internet of Things - ELE Times

Hardware-based Computer Security Techniques to Defeat Hackers: From Biometrics to Quantum Cryptography: Dube, Roger R.: 9780470193396: Amazon.com: Books
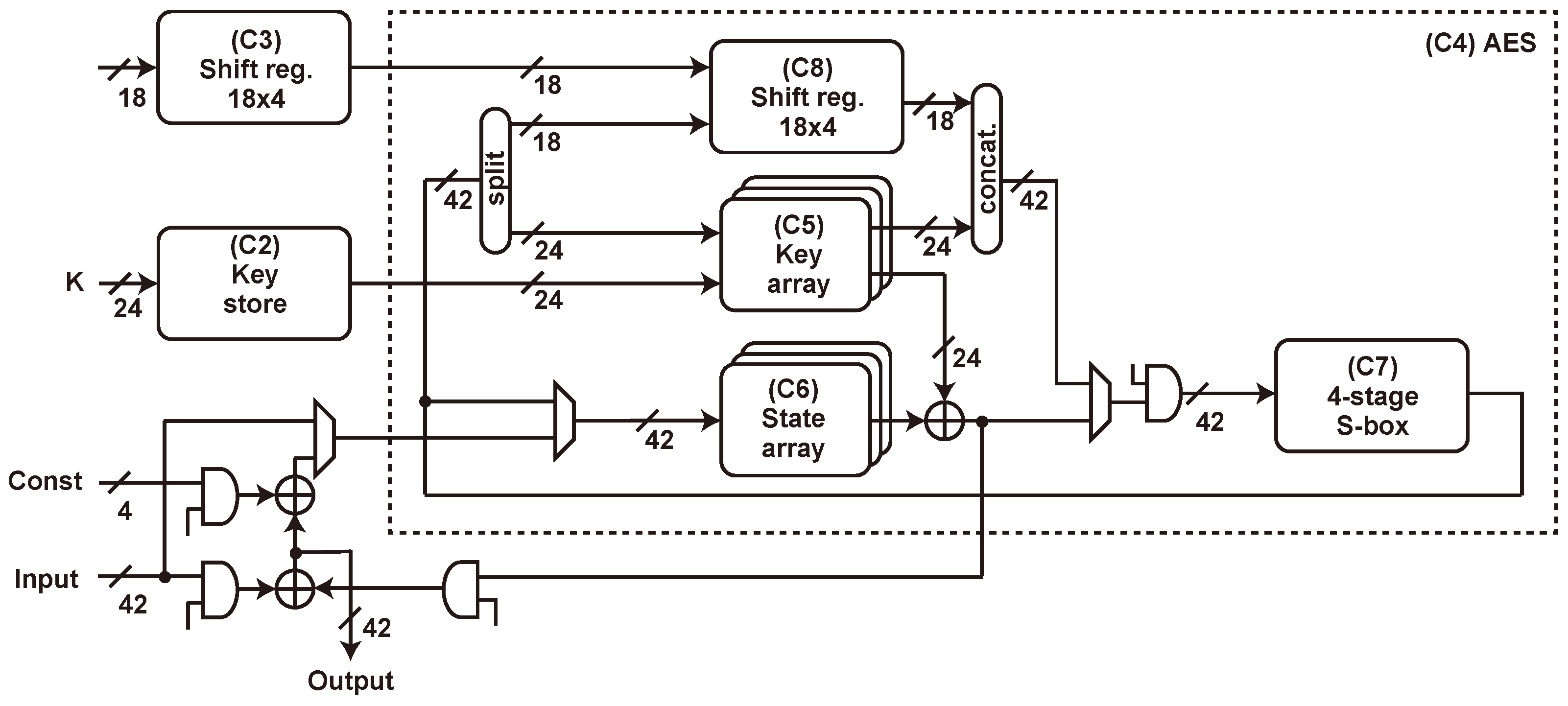
Cryptography | Free Full-Text | Hardware Performance Evaluation of Authenticated Encryption SAEAES with Threshold Implementation