
Seal One on Twitter: "Seal One Hardware Devices #PSD2, #SCA, #2FA, #signature https://t.co/8YAGS6Jvz9" / Twitter
RSA Token. Two-factor Authentication Device, Hardware. Cryptosystem for Security. Vector Icon Stock Vector - Illustration of protection, object: 147897133







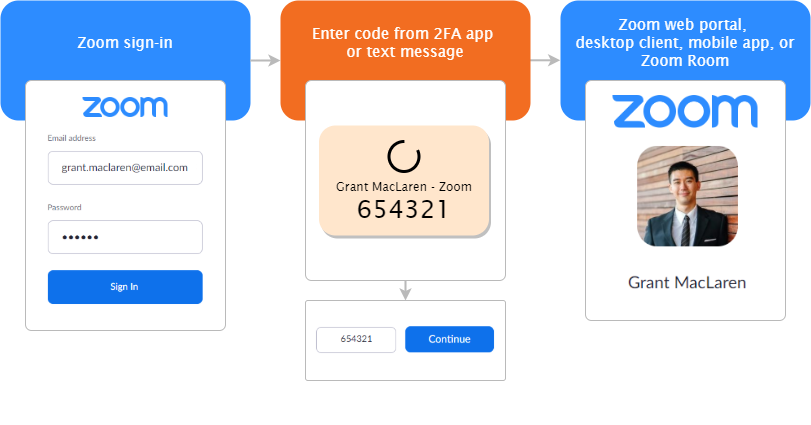


/cdn.vox-cdn.com/uploads/chorus_asset/file/14155906/akrales_190220_3226_0003.jpg)









